Whitepaper: Secure Remote Support Tools for Windows Environments
Executive Summary
In modern IT operations, secure remote support is essential for effective system administration, end-user support, and incident resolution. This whitepaper provides a comprehensive overview of leading remote support tools for Windows environments, focusing on their security capabilities, compliance readiness, and suitability for different organizational needs.
1. Introduction
The increasing shift towards distributed workforces and remote management demands robust remote support solutions. However, these tools introduce potential attack vectors, making security a paramount concern.
This whitepaper evaluates five widely-used remote support tools, comparing their security features, deployment options, compliance adherence, and scalability, and provides implementation best practices.
2. Evaluation Criteria
Each tool is assessed based on:
- Encryption Protocols
- Authentication & MFA Support
- Access Control & Permission Management
- Session Logging & Auditing
- Compliance Certifications
- Deployment Options (Cloud/Self-Hosted)
- Cost Considerations
3. Remote Support Tools Overview
3.1 AnyDesk (On-Premises Option)
- Encryption: TLS 1.2 + RSA 2048 key exchange.
- Authentication: Supports Two-Factor Authentication (TOTP, SAML).
- Access Control: Whitelisting, session permission customization.
- Logging: Basic session logs, optional recording.
- Deployment: On-Premises or Cloud.
- Compliance: GDPR, ISO 27001 compatible (with correct configuration).
- Best For: SMBs and Enterprises needing a lightweight, customizable, and secure solution.
For more details, refer to the AnyDesk Documentation.
3.2 TeamViewer Tensor
- Encryption: AES-256-bit encryption with RSA key exchange.
- Authentication: SAML-based Single Sign-On (SSO), Two-Factor Authentication.
- Access Control: Granular permission sets.
- Logging: Full session recording, audit logs.
- Deployment: Cloud (with Enterprise options for isolated environments).
- Compliance: ISO 27001, SOC2, GDPR, HIPAA.
- Best For: Large enterprises seeking a cloud-first approach with strong compliance adherence.
For more details, refer to the TeamViewer Documentation.
3.3 ConnectWise Control (Self-Hosted)
- Encryption: SSL/TLS with AES-256 encryption.
- Authentication: SAML, LDAP, TOTP, RADIUS integrations.
- Access Control: Highly granular roles, per-session permissions.
- Logging: Comprehensive audit logging, session recordings.
- Deployment: Self-Hosted or Cloud.
- Compliance: SOC 2, HIPAA, GDPR friendly.
- Best For: MSPs, IT service providers, and enterprises needing tight control.
For more details, refer to the ConnectWise Control Documentation.
3.4 BeyondTrust Remote Support (Bomgar)
- Encryption: TLS 1.2 with AES-256 encryption.
- Authentication: Full MFA suite (SAML, RADIUS, Duo, etc.).
- Access Control: Role-based, detailed permission control.
- Logging: Extensive session recording, robust audit trails.
- Deployment: Self-Hosted (Physical or Virtual Appliance).
- Compliance: PCI-DSS, HIPAA, GDPR, ISO/IEC 27001.
- Best For: Enterprises with strict security/compliance mandates.
For more details, refer to the BeyondTrust Remote Support Documentation.
3.5 Microsoft RDP + RD Gateway + MFA
- Encryption: TLS + Network Level Authentication (NLA).
- Authentication: Integrates with Azure AD MFA, smart cards, RADIUS.
- Access Control: Group Policies, Firewall Rules, Conditional Access.
- Logging: Configurable via Event Viewer, integrates with SIEM.
- Deployment: Fully On-Premises.
- Compliance: Configurable to meet GDPR, ISO, HIPAA.
- Best For: Organizations preferring in-house, cost-effective solutions with full control.
For more details, refer to the Microsoft Secure RDP Deployment Best Practices.
4. Security Comparison Summary
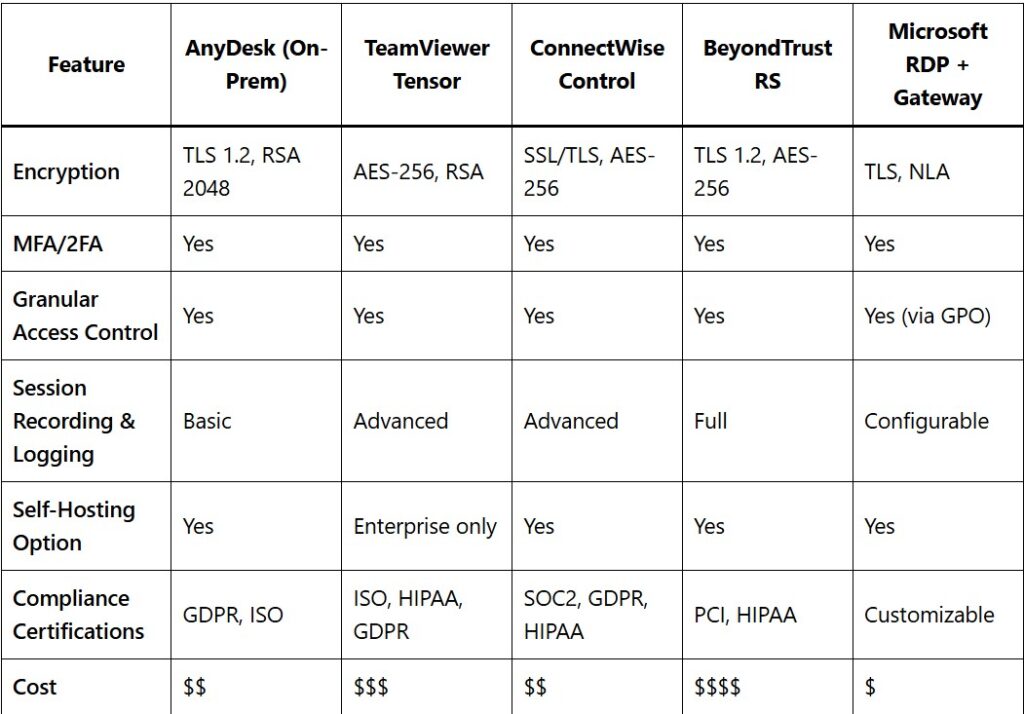
5. Best Practices for Secure Deployment
- Enable MFA: Always enforce multi-factor authentication across all remote tools.
- Use Strong Encryption Standards: Prefer TLS 1.2+ with AES-256 wherever possible.
- Restrict Access: Implement role-based access, IP whitelisting, and firewall rules.
- Audit & Record Sessions: Enable full session logging and recording to ensure accountability.
- Patch Regularly: Keep remote support tools up to date with the latest security patches.
- Integrate with SIEM: Forward logs to centralized security monitoring solutions.
- Deploy On-Prem Where Needed: For highly sensitive environments, self-hosted solutions provide maximum control.
6. Conclusion
Selecting the right remote support tool hinges on balancing security, compliance requirements, cost, and deployment preferences. Enterprises handling sensitive data or subject to strict regulatory standards should consider BeyondTrust or ConnectWise Control (Self-Hosted). For organizations prioritizing ease of use while maintaining robust security, AnyDesk On-Prem or TeamViewer Tensor are excellent options. Meanwhile, Microsoft RDP with hardened configurations remains a cost-effective and secure choice for internal IT teams.
7. References & Further Reading
- NIST Cybersecurity Framework A voluntary framework consisting of standards, guidelines, and best practices to manage cybersecurity-related risks.
- ISO/IEC 27001 Standards Overview International standard for managing information security and risk.
- PCI DSS Compliance Guidelines Standards designed to ensure all companies that process, store, or transmit credit card information maintain a secure environment.
- HIPAA Security Rule Overview Regulations to safeguard electronic protected health information (ePHI).
- Microsoft Secure RDP Deployment Best Practices Microsoft’s guidance for securing Remote Desktop Services (RDS) deployments.
- AnyDesk Security Documentation Details on AnyDesk’s security mechanisms and encryption protocols.
- TeamViewer Security Statement Explanation of TeamViewer’s approach to encryption, authentication, and compliance.
- ConnectWise Control Security Overview Describes ConnectWise Control’s security posture and available controls.
- BeyondTrust Remote Support Security Guide Overview of BeyondTrust’s security model and compliance features.






